What Is Decentralized Identity And How Does It Protect Privacy
Imagine a world where you have complete control over your personal data, and you’re not at the mercy of giant corporations who can decide what to do with it. Sounds utopian, right? But what if I told you that this world is slowly taking shape, thanks to a groundbreaking concept called decentralized identity.
- Unlocking The Power Of Passive Income: Top Crypto Projects To Consider
- Evaluating A Crypto Exchange: Navigating The Complex World Of Digital Assets
- Embracing The Crypto Revolution: 5 Nations Leading The Way For Investors
- Clear Visibility And Unshakeable Trust: How Blockchain Illuminates Supply Chain Operations
- The Evolution Of Financial Discretion Unraveling The Mystery Of Privacy Coins
In simple terms, decentralized identity is an approach to managing our identities online that puts the power back in our hands. No more centralized databases storing all our sensitive information, waiting to be hacked or exploited. No more relying on third-party services to authenticate us, only to compromise our data in some way. Decentralized identity promises to give us, the users, the autonomy to decide what we want to share, with whom, and how.
So, how does it work?
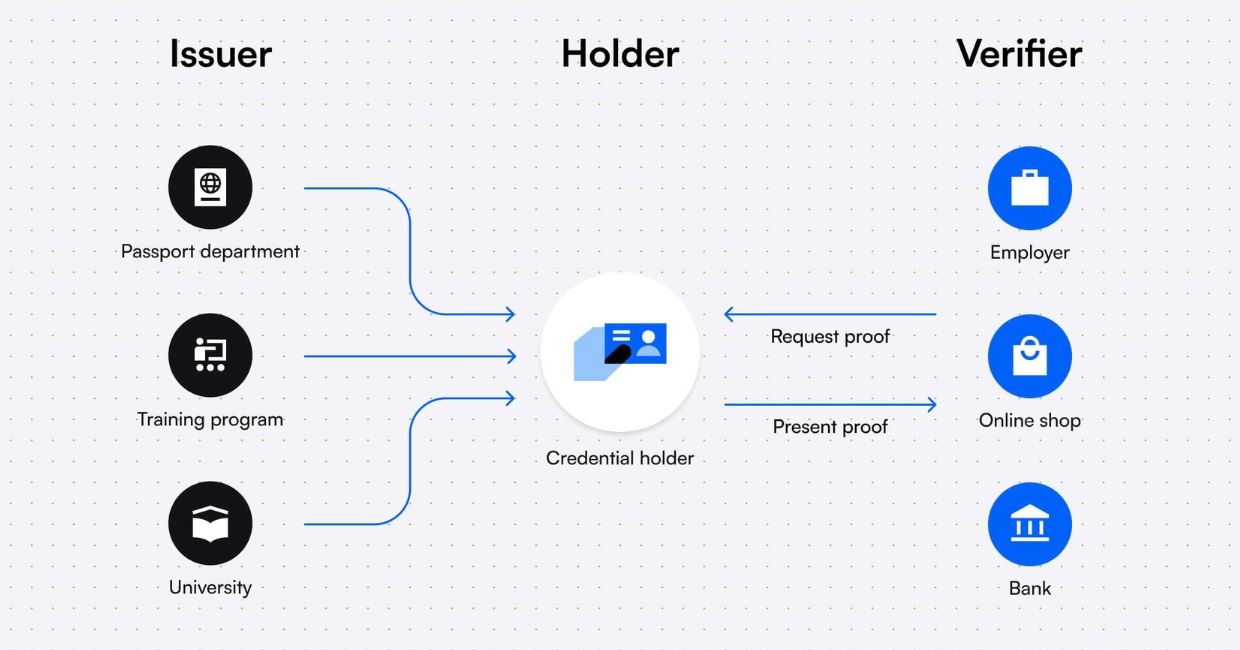
The core idea behind decentralized identity is that individuals should have full control over their digital identities. This means that instead of relying on centralized authorities like Facebook or Google to manage our identities, we use self-managed digital identities that are portable, flexible, and user-centric.
Here’s an analogy to help illustrate the concept: think of your digital identity like your physical wallet. Just as you carry your wallet with you wherever you go, storing your cash, cards, and ID documents, a decentralized identity is like carrying your own digital wallet that contains your personal data and credentials. But, unlike traditional wallets, this one is virtual and a lot more secure.
When you want to use a service or app, you simply "show" your digital wallet (in other words, present your credentials) to the service provider. But, just like you wouldn’t hand over your entire wallet to a stranger, you only share the specific information required by the service. The beauty of decentralized identity lies in the granularity of control. You, as the user, get to decide exactly what you’re sharing, and for how long.
Now, let’s talk about how this approach can better protect our online privacy.
Enhanced data protection
Traditional centralized systems typically store our data in a monolithic database. This creates a massive attack surface, where a single breach can expose countless amounts of sensitive information. In contrast, decentralized identity distributes the storage of our personal data across many nodes in a peer-to-peer network or blockchain. This makes it extremely difficult for attackers to access our data in one go.
Reducing reliance on intermediaries
By taking away the middlemen who manage our identities, we reduce the risk of data compromises that occur through third-party breaches. For example, if someone hacks into a social media company’s database, our information is safer because we’ve stored our credentials securely in our personal wallets.
Minimizing data exposure
Decentralized identity allows for something called "selective disclosure." This means we can reveal only the information required for a specific task, reducing the risk of over-sharing or over-exposure of our sensitive information. Imagine, for instance, being asked to show your full passport number just to sign up for an online shopping site!
In conclusion, decentralized identity is a powerful approach to digital identity management that puts the control squarely in the user’s hands. By distributing the storage and management of our personal data across devices, reducing reliance on intermediaries, and enabling granular control over what we share, decentralized identity promises to bring a new wave of online protection to users worldwide. The world we thought was utopian is now looking more like a technological leap that could very well redefine the way we live our online lives.
